In these Behind the Magic series, we give an overview of what we worked on the month before. Please be warned that the contents might get a little technical now and then.
At Athom we're all excited for Homey v2.0.
The Homey Community is excited for Homey v2.0.
Everyone is excited for Homey v2.0!
There's only one road blocker standing in between before we can start rolling out Homey v2.0 to our internal alpha testers, then experimental and finally to everyone. And that's Homey v1.5.13 to be stable.
A small recap: Homey v1.5.13 included a major microcontroller update, which has improved overall reliability and signal reception. There are a few 433 MHz protocols doing quirky things though, and they stopped working after the upgrade. So we first have to iron these out, then release Homey v1.5.13 to stable, and then finally we can start testing Homey v2.0.
In the meantime, we've done many other things to prepare the Homey v2.0 release. One that I'd like to highlight are security updates across the entire Homey ecosystem.
OAuth2 Login
The first one is something you maybe have already noticed. The login screen has changed in that you can now give access to specific Homeys to a 3rd party app. For example, if you had more than one Homey and wanted to use the Amazon Alexa integration, you'd have to say 'Alexa, select a Homey'. That's now changed to a simple radio button during the authentication.
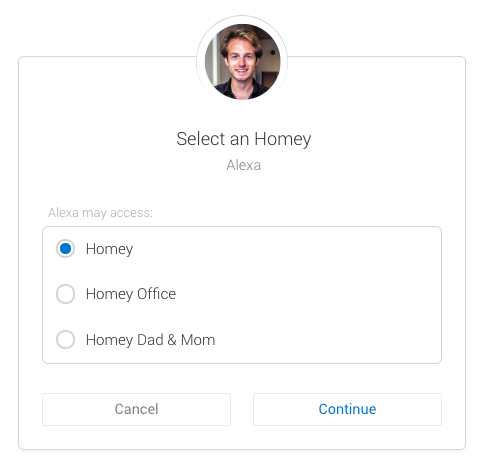
Of course, not many people have more than one Homey so this example isn't really recognisable. What this update does behind the scenes is a lot more interesting. I've talked before about the Web API, and that it opens up new possibilities for Community Developers to create Homey integrations that not only run on Homey, but also somewhere else. Examples are IFTTT, HomeyScript, Google Assistant etc.
We've created the first few building blocks towards a complete open system where you can give delegated access to someone else's cloud integration. It's similar to 'Log-in with Facebook', where you can decide if the app can post to your Timeline, for example.
With this update, we've also got rid of the static keys that Homey v1.x uses. Homey v2.0 uses something called rolling sessions, which increases security even more.
Local HTTPS
Another security improvement we've built is local HTTPS. When you're at home and connected to your Wi-Fi, Homey prefers a local connection (e.g. http://192.168.1.100) over a cloud connection (https://abcdef1234.homey.athom.com).
The problem with local HTTPS is that it requires a domain name, thus IP addresses do not work. Currently, in Homey v1.x, the communication with Homey and your phone is unencrypted when you're on your own Wi-Fi network. We consider your home's network as trusted, but still, it wasn't good enough for us.
Then we came up with something very unique. We've created a custom DNS server that resolves any domain name to an IP address. For example, 192-168-1-100.unique-id.homeylocal.com points to 192.168.1.100. Now you can visit any local IP with a domain name! Step two was to create a unique SSL certificate for every Homey, namely *.unique-id.homeylocal.com. Now we can visit https://192-168-1-100.unique-id.homeylocal.com over a secure connection, locally.
![]()
Next to it obviously being safer, is this also useful when visiting websites talking to Homey, e.g. https://developer.athom.com. Browsers don't allow HTTP networking from a HTTPS website (and rightly so), and with this feature we can require that all 3rd party integrations are used over HTTPS, to make your Homey even safer.
The local SSL functionality is available for all Homeys running v2.0 and above.
Other things
We've released updates to the Sonos, Soundboard, Nanoleaf, IFTTT apps and updates for Fibaro, Aeotec, KNX, KlikAanKlikUit and others are currently being tested. We're also working on a better Knowledge Base to accompany Homey v2.0.